Identifying Authorized Websites
today’s digital age, internet users encounter countless websites daily. While most websites are legitimate and trustworthy, there is a growing concern about unauthorized individuals attempting to create fake websites with identical layouts to deceive users. This practice, known as phishing or website impersonation, can have serious consequences for unsuspecting users. In this article, we will explore the methods to identify authorized websites, the potential risks of website impersonation, and the best practices to protect yourself and your users against such threats.
Understanding Website Impersonation and its Dangers
What is Website Impersonation? Website impersonation is a deceptive tactic used by cybercriminals to create fake websites that mimic the appearance and design of legitimate websites. The main objective of these malicious websites is to trick users into revealing sensitive information, such as login credentials, financial details, or personal data. Impersonation can occur across various online platforms, including email, social media, and search engines.
Attackers employ sophisticated techniques to make their fake websites appear authentic, often using slight variations in domain names or URLs that closely resemble the original site. They may also replicate the official branding, logos, and layout of the genuine website to lure unsuspecting users into believing they are interacting with a trusted entity.
The Dangers of Website Impersonation Website impersonation poses significant risks to both individuals and organizations. Understanding these dangers is crucial in recognizing the importance of identifying and avoiding such fraudulent activities.
Must read……
How to extract data from website using python web crawler
Financial Losses: Users who unknowingly submit their financial information on fake websites can fall victim to credit card fraud, identity theft, or unauthorized transactions, leading to substantial financial losses.
Reputational Damage: For businesses, website impersonation can severely impact their reputation. If customers inadvertently share sensitive data on fake websites, they may hold the legitimate organization responsible for the consequences, damaging trust and credibility.
Data Breaches: Impersonation attacks can result in data breaches, exposing sensitive information that can be exploited for further cybercrimes or sold on the dark web.
Identifying Authorized /Genuine Websites
Domain Verification One of the primary steps in recognizing authorized websites is verifying the domain name. Scammers often create deceptive domain names that resemble the official domain of an organization. To ensure a website’s legitimacy, users should:
Check the spelling and syntax of the domain name: Carefully examine the URL for slight misspellings, additional characters, or hyphenation that may indicate an impersonation attempt.
Verify the top-level domain (TLD): Genuine government websites in India usually have “.gov.in” as their TLD, while educational institutions have “.ac.in” and non-profit organizations “.org.in.” Be cautious if the TLD seems inconsistent with the website’s claimed identity.

Look for subdomains: Ensure that the subdomains (e.g., “subdomain.website.com”) are consistent with the main domain and not suspiciously unrelated.
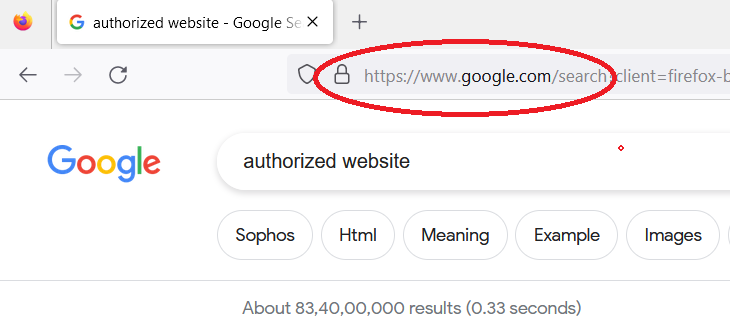
Check for SSL Certificates: Legitimate websites often use Secure Sockets Layer (SSL) certificates, which can be identified by the “HTTPS” in the URL and a padlock icon in the address bar. SSL ensures that the connection between the user and the website is encrypted, enhancing security and protecting against data interception.
By following these steps, users can significantly reduce the risk of falling prey to phishing attempts and website impersonation.
Website Content and Design Authentic websites typically maintain a high standard of content and design consistency. When analyzing a website for legitimacy, users should:
Thoroughly review the content: Look for grammatical errors, awkward language, or poorly constructed sentences, as fake websites often contain language mistakes that official websites would not have.
Examine branding and layout: Check if the website’s branding, logos, and overall layout match the ones displayed on the organization’s official communications. Discrepancies may indicate an impersonation attempt.
Verify Contact Information: Genuine websites provide valid contact information, including physical addresses and phone numbers. Verify this information with the organization’s official records or directories.
Scrutinize images and multimedia: Fake websites might use generic or stock images, while official websites are more likely to feature original content.
By paying attention to these details, users can identify red flags and distinguish between authorized websites and malicious ones.
Check HTTPS and Padlock Icon When visiting a website, always ensure the presence of “HTTPS” in the URL and a padlock icon in the address bar. These indicators signify a secure connection and encrypted data transmission, providing an added layer of protection against eavesdropping and man-in-the-middle attacks.
Avoid submitting sensitive information, such as login credentials or credit card details, on websites that do not have a valid HTTPS certificate. If you encounter a website that claims to be secure but lacks these indicators, exercise caution and refrain from sharing any sensitive data.
Monitor Domain Registrations To protect their brand and users from impersonation attempts, website owners should proactively monitor domain registrations. Registering variations of their official domain can prevent cybercriminals from using similar domains for impersonation.
Consider registering common misspellings or popular TLDs associated with your organization to reduce the likelihood of phishing attacks. Moreover, regularly reviewing new domain registrations that bear resemblance to your website’s domain is essential to detect potential impersonation attempts early on.
Implement DMARC, SPF, and DKIM Email-based impersonation attacks, commonly known as email spoofing, are prevalent in phishing campaigns. To combat this threat, website owners can implement email authentication protocols like Domain-based Message Authentication, Reporting, and Conformance (DMARC), Sender Policy Framework (SPF), and Domain Keys Identified Mail (DKIM).
DMARC helps prevent the delivery of fraudulent emails by specifying the actions to take when an email fails authentication checks. SPF and DKIM verify the authenticity of the sender’s domain and ensure that email messages are not tampered with during transmission.
By deploying these email authentication protocols, website owners can protect their users from falling victim to email-based impersonation scams.
Regularly Update Website Content Attackers may take advantage of outdated information on legitimate websites to construct convincing impersonation attempts. Website owners must regularly update their website’s content and ensure that critical announcements, policies, and contact details are current.
Consider implementing a content review schedule to maintain accurate information, especially regarding events, services, or promotions. Regularly review the website’s footer, About Us, and Contact Us sections to prevent inconsistencies that impersonators could exploit.
Educate Users about Impersonation Risks As part of an overall security awareness strategy, website owners should educate their users about website impersonation risks and provide guidelines on how to verify website authenticity. Some effective measures include:
- Publishing security awareness articles on the website.
- Sending out periodic email newsletters with security tips.
- Displaying website banners or pop-ups that remind users to stay vigilant against phishing attempts.
Empowering users with knowledge helps them recognize suspicious activities and be cautious while interacting with websites, thereby reducing the success rate of impersonation attempts.
Reporting Impersonation Attempts
Reporting to Authorities Reporting impersonation attempts to relevant authorities is crucial in combating cybercrime. In India, the Computer Emergency Response Team of India (CERT-In) is the designated agency responsible for handling cybersecurity incidents. Users who encounter suspicious websites or emails should promptly report them to CERT-In for investigation and potential action against the perpetrators.
The official CERT-In website provides guidelines on how to report cybersecurity incidents, including phishing attempts and website impersonation.
Browser Reporting Mechanisms Popular web browsers often include built-in reporting mechanisms that allow users to flag potentially dangerous websites. By reporting suspicious sites, users can help browser developers improve their security features and warn other users about potential threats.
Web browsers may use community-driven blocklists to prevent users from accessing reported malicious websites, offering an additional layer of protection against website impersonation.
at last website impersonation is a growing threat that requires vigilance and proactive measures to combat effectively. By understanding the signs of website impersonation and implementing best practices, users can protect themselves and others from falling victim to these deceptive practices.
For website owners, safeguarding their brands and users against impersonation attempts involves proactive domain monitoring, email authentication, regular content updates, and user education. Together, these strategies create a safer online environment for everyone, building trust and confidence in the digital landscape.
Remember, cybersecurity is an ongoing effort. Staying informed about the latest threats and regularly reviewing security measures is vital to maintaining the integrity and safety of online interactions. By working together as a community, we can collectively strengthen our defenses against website impersonation and other cyber threats.
Must Read….
How to Unblock ICICI debit card